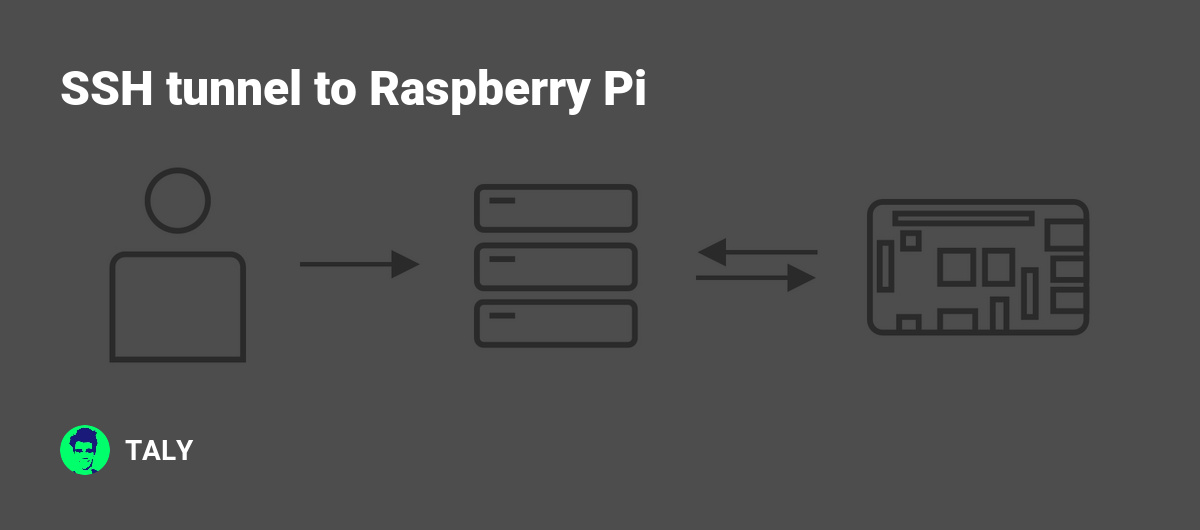
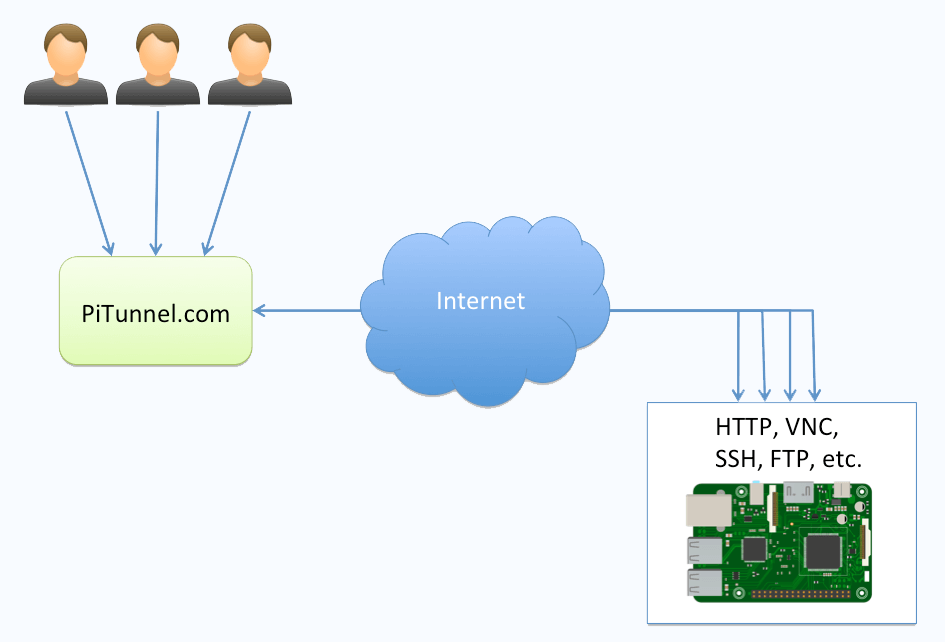
Secure remote access is crucial in today's digital world, and Raspberry Pi SSH tunnel has emerged as a powerful tool for achieving it. Whether you're a developer, hobbyist, or IT professional, understanding how to set up and use an SSH tunnel on Raspberry Pi can significantly enhance your security and flexibility. This comprehensive guide will walk you through everything you need to know about Raspberry Pi SSH tunnel, from the basics to advanced configurations.
Raspberry Pi SSH tunneling allows users to create encrypted connections between devices, ensuring that sensitive data remains protected during transmission. This technology is particularly useful for accessing remote servers, bypassing firewalls, or securely transferring files. In this article, we'll explore the benefits, setup process, troubleshooting tips, and best practices for using SSH tunnels with Raspberry Pi.
As cybersecurity threats continue to evolve, securing your network and data is more important than ever. By leveraging Raspberry Pi's capabilities and the power of SSH tunneling, you can establish a robust and secure connection that protects your privacy and enhances productivity. Let's dive deeper into the world of Raspberry Pi SSH tunneling and discover how it can benefit you.
Read also:Explore The World Of Entertainment With Hdhub4utoday Your Ultimate Guide
Table of Contents:
- Introduction to Raspberry Pi SSH Tunnel
- Benefits of Using Raspberry Pi SSH Tunnel
- Setting Up Raspberry Pi SSH Tunnel
- Configuring SSH Tunnel
- Troubleshooting Common Issues
- Advanced Configurations
- Security Best Practices
- Alternatives to Raspberry Pi SSH Tunnel
- Use Cases for Raspberry Pi SSH Tunnel
- Conclusion
Introduction to Raspberry Pi SSH Tunnel
Raspberry Pi SSH tunnel is a secure method of connecting to remote devices or networks. SSH (Secure Shell) is a cryptographic network protocol that enables encrypted communication between devices, making it ideal for remote access and file transfer. When combined with Raspberry Pi, this technology becomes a powerful tool for hobbyists, developers, and IT professionals alike.
Why Use Raspberry Pi for SSH Tunneling?
Raspberry Pi offers several advantages for SSH tunneling:
- Cost-effective: Raspberry Pi is an affordable single-board computer that can be used for a variety of applications.
- Compact and portable: Its small form factor makes it easy to set up and deploy in different environments.
- Energy-efficient: Raspberry Pi consumes minimal power, making it suitable for long-term use.
- Community support: Raspberry Pi has a vast community of users who contribute to its development and provide resources for learning and troubleshooting.
Benefits of Using Raspberry Pi SSH Tunnel
Raspberry Pi SSH tunnel provides numerous benefits, including:
- Enhanced security: Encrypts data transmission, protecting sensitive information from unauthorized access.
- Remote access: Allows users to access remote devices or networks securely.
- File transfer: Facilitates secure file transfers between devices.
- Firewall bypass: Enables users to bypass restrictive firewalls and access blocked websites or services.
Setting Up Raspberry Pi SSH Tunnel
Setting up Raspberry Pi SSH tunnel involves several steps. Below is a detailed guide to help you get started:
Step 1: Install Raspberry Pi OS
Begin by installing Raspberry Pi OS on your Raspberry Pi. You can download the latest version from the official Raspberry Pi website. Once installed, connect your Raspberry Pi to a monitor, keyboard, and mouse to configure it.
Read also:Secure And Convenient Parking At John Wayne Airport Your Guide To Hasslefree Travel
Step 2: Enable SSH
SSH is disabled by default on Raspberry Pi OS. To enable it, follow these steps:
- Open the Raspberry Pi Configuration tool by typing "sudo raspi-config" in the terminal.
- Select "Interfacing Options" and enable SSH.
- Reboot your Raspberry Pi for the changes to take effect.
Step 3: Set Up the SSH Tunnel
To set up the SSH tunnel, use the following command in the terminal:
ssh -L [local_port]:[destination_host]:[destination_port] [username]@[raspberry_pi_ip]
Configuring SSH Tunnel
Once the basic setup is complete, you can configure your Raspberry Pi SSH tunnel to suit your needs. Below are some common configurations:
Dynamic Port Forwarding
Dynamic port forwarding allows you to use Raspberry Pi as a SOCKS proxy server. This is useful for bypassing firewalls or accessing blocked websites. To enable dynamic port forwarding, use the following command:
ssh -D [local_port] [username]@[raspberry_pi_ip]
Reverse SSH Tunnel
A reverse SSH tunnel enables you to access your Raspberry Pi from a remote location, even if it's behind a firewall. To set up a reverse SSH tunnel, use the following command:
ssh -R [remote_port]:localhost:[local_port] [username]@[remote_server_ip]
Troubleshooting Common Issues
While setting up Raspberry Pi SSH tunnel, you may encounter some common issues. Below are solutions to these problems:
Connection Refused
If you receive a "connection refused" error, ensure that SSH is enabled on your Raspberry Pi and that the correct IP address and port number are being used.
Authentication Failed
If authentication fails, verify that the username and password are correct. You can also try using SSH keys for authentication instead of passwords.
Advanced Configurations
For advanced users, there are several ways to enhance your Raspberry Pi SSH tunnel:
SSH Key Authentication
Using SSH keys for authentication is more secure than passwords. To set up SSH key authentication, follow these steps:
- Generate a key pair on your local machine using the command: ssh-keygen
- Copy the public key to your Raspberry Pi using the command: ssh-copy-id [username]@[raspberry_pi_ip]
- Disable password authentication by editing the SSH configuration file: sudo nano /etc/ssh/sshd_config
SSH Tunneling with Multiple Hops
For more complex setups, you can create SSH tunnels with multiple hops. This is useful for accessing devices behind multiple firewalls or networks. Use the following command:
ssh -L [local_port]:[destination_host]:[destination_port] -J [jump_host] [username]@[raspberry_pi_ip]
Security Best Practices
To ensure the security of your Raspberry Pi SSH tunnel, follow these best practices:
- Use strong passwords or SSH keys for authentication.
- Limit SSH access to specific IP addresses using the SSH configuration file.
- Regularly update your Raspberry Pi OS and SSH software to protect against vulnerabilities.
- Monitor SSH logs for suspicious activity.
Alternatives to Raspberry Pi SSH Tunnel
While Raspberry Pi SSH tunnel is a popular choice, there are other alternatives you can consider:
- VPN: Virtual Private Networks provide encrypted connections between devices and networks.
- SSH clients: Software like PuTTY or OpenSSH can be used for SSH tunneling on different platforms.
- Cloud-based solutions: Services like AWS or Azure offer secure remote access solutions.
Use Cases for Raspberry Pi SSH Tunnel
Raspberry Pi SSH tunnel has numerous applications across various industries. Some common use cases include:
- Remote server management
- Secure file transfer
- Firewall bypass
- Home automation and IoT devices
- Secure browsing
Conclusion
Raspberry Pi SSH tunnel is a powerful tool for secure remote access and data transmission. By following the steps outlined in this guide, you can set up and configure your Raspberry Pi SSH tunnel to meet your specific needs. Remember to adhere to security best practices and regularly update your system to protect against potential threats.
We encourage you to share your experiences and tips in the comments section below. Additionally, feel free to explore other articles on our website for more information on Raspberry Pi and related technologies. Together, let's build a safer and more connected digital world!
Data Sources: