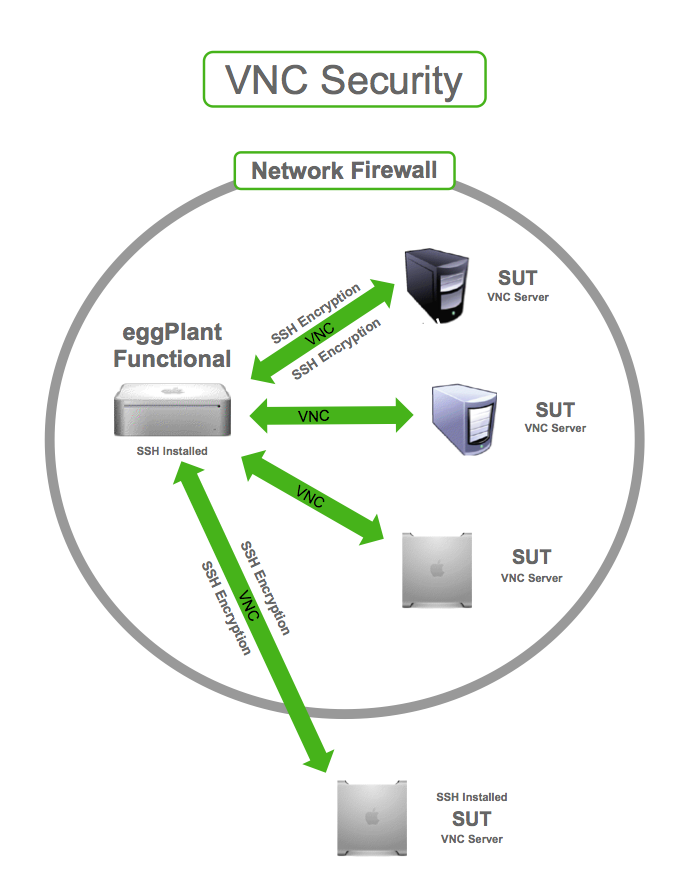
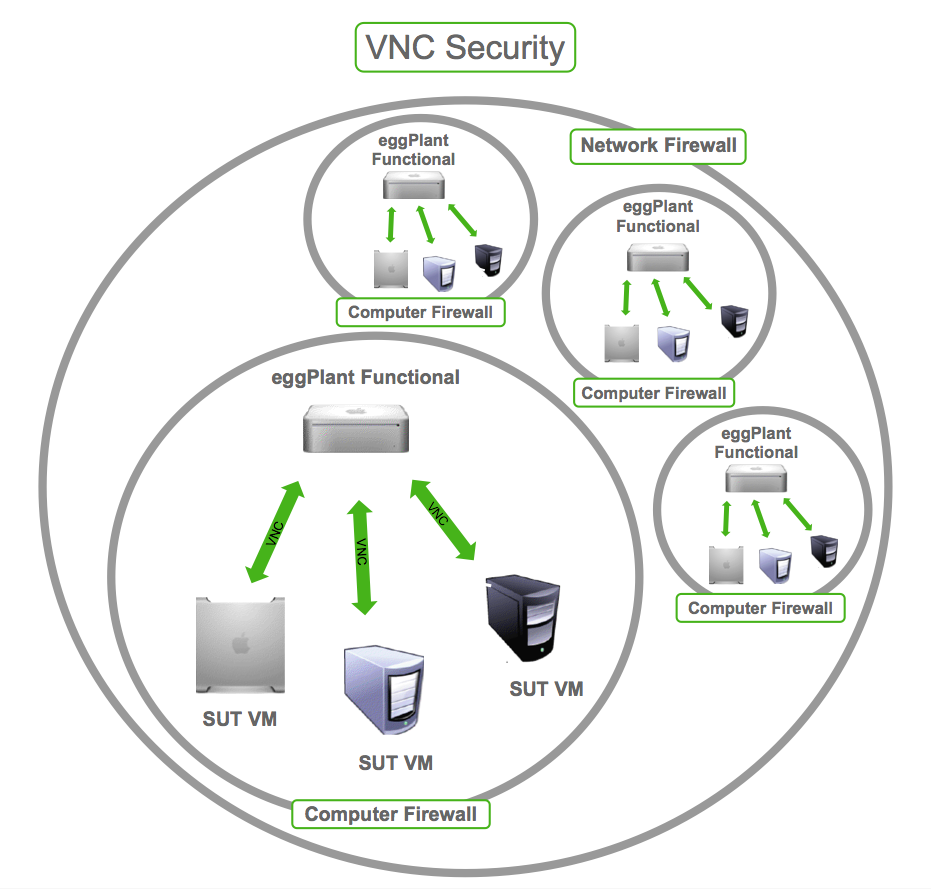
Securing your RPi3 VNC server is crucial to protect sensitive data and maintain system integrity. As remote access solutions become increasingly popular, ensuring robust security measures is essential to prevent unauthorized access and potential cyber threats. By following best practices and implementing advanced security protocols, you can safeguard your RPi3 VNC server effectively.
VNC (Virtual Network Computing) allows users to remotely access and control a Raspberry Pi 3 (RPi3) from another device. However, this convenience comes with inherent risks if proper security measures are not in place. This guide will walk you through the steps to enhance the security of your RPi3 VNC server, ensuring it remains protected against potential vulnerabilities.
Whether you're a hobbyist, a small business owner, or an IT professional, securing your RPi3 VNC server is vital to safeguard your digital assets. This article will cover everything from basic security practices to advanced configurations, ensuring your setup is as secure as possible.
Read also:Ivo Graham Wife Carrie Matthews A Comprehensive Look Into Their Life And Relationship
Understanding the Importance of Security for RPi3 VNC Server
Why Security Matters for RPi3 VNC Server
Remote access tools like VNC provide immense flexibility but also introduce security risks. Without proper safeguards, your RPi3 VNC server can become a target for cybercriminals. Unauthorized access can lead to data breaches, system corruption, or even complete takeover of your device.
Key risks associated with insecure VNC setups include:
- Brute force attacks targeting weak passwords
- Exploitation of unpatched vulnerabilities
- Data interception during transmission
- Unauthorized access leading to data theft
Implementing strong security measures ensures your RPi3 VNC server remains protected while maintaining its functionality.
Basic Security Measures for RPi3 VNC Server
Setting Up Strong Passwords
Creating strong passwords is the first line of defense for your RPi3 VNC server. Avoid using simple or easily guessable passwords. Instead, opt for complex combinations that include uppercase and lowercase letters, numbers, and special characters.
Best practices for password management include:
- Using a minimum length of 12 characters
- Avoiding common dictionary words
- Enabling password expiration policies
- Implementing multi-factor authentication (MFA)
By adhering to these guidelines, you significantly reduce the risk of unauthorized access through password-based attacks.
Read also:Comprehensive Guide To Setting Up Ssh On Iot Devices And Routers
Advanced Security Configurations for RPi3 VNC Server
Implementing Encryption Protocols
Encrypting VNC communications ensures data transmitted between your RPi3 and remote devices remains secure. Use protocols like TLS/SSL to encrypt all VNC sessions. This prevents eavesdropping and data interception by malicious actors.
Steps to implement encryption:
- Install SSL certificates on your RPi3
- Configure VNC server to use encrypted connections
- Verify certificate authenticity
Encryption not only protects data in transit but also enhances overall security posture.
Firewall Configuration for Enhanced Security
Setting Up Firewall Rules
A properly configured firewall acts as a barrier between your RPi3 VNC server and potential threats. Limit access to only trusted IP addresses and block unnecessary ports to minimize attack surfaces.
Firewall configuration tips:
- Allow VNC traffic only on specific ports
- Block all unauthorized incoming connections
- Regularly update firewall rules
By fine-tuning firewall settings, you create an additional layer of protection for your RPi3 VNC server.
User Access Management for RPi3 VNC Server
Managing User Permissions
Restricting user access based on roles and responsibilities ensures only authorized individuals can interact with your RPi3 VNC server. Implement role-based access control (RBAC) to define permissions clearly.
User management best practices:
- Create separate accounts for each user
- Grant minimal necessary permissions
- Monitor user activity regularly
Proper user access management reduces the likelihood of accidental or intentional misuse of system resources.
Regular Updates and Patch Management
Keeping Software Up-to-Date
Regularly updating your RPi3's operating system and VNC server software ensures all known vulnerabilities are patched promptly. Automated update mechanisms can simplify this process, ensuring your system remains secure.
Update management strategies:
- Enable automatic updates
- Test updates in a staging environment
- Document update history
Staying current with updates minimizes exposure to newly discovered threats.
Monitoring and Logging for RPi3 VNC Server
Implementing Logging and Monitoring
Monitoring system logs provides valuable insights into potential security incidents. Configure logging to capture relevant information and set up alerts for suspicious activities.
Logging and monitoring recommendations:
- Enable detailed logging for VNC sessions
- Set up alert notifications for unusual activities
- Regularly review logs for anomalies
Proactive monitoring helps identify and address security issues before they escalate.
Backup Strategies for RPi3 VNC Server
Creating Regular Backups
Backing up your RPi3 VNC server ensures data recovery is possible in case of a security breach or system failure. Implement automated backup solutions to streamline this process.
Backup best practices:
- Store backups in secure locations
- Test backup restoration periodically
- Encrypt backup files
Reliable backup strategies safeguard your data and minimize downtime during recovery.
Testing Security Configurations
Conducting Security Audits
Regularly testing your security configurations ensures all measures remain effective. Use tools like vulnerability scanners and penetration testing to identify weak points.
Security testing procedures:
- Perform routine vulnerability scans
- Engage third-party auditors for assessments
- Document findings and implement improvements
Thorough testing reinforces your security posture and addresses emerging threats.
Best Practices for Long-Term Security
Sustaining Security Efforts
Maintaining long-term security requires ongoing commitment and vigilance. Stay informed about the latest security trends and adapt your strategies accordingly.
Long-term security tips:
- Follow security news and updates
- Participate in security communities
- Review and refine security policies regularly
Consistent effort ensures your RPi3 VNC server remains secure against evolving threats.
Conclusion
Securing your RPi3 VNC server involves implementing a combination of basic and advanced security measures. From setting strong passwords to conducting regular security audits, each step contributes to a robust security framework. By following the guidelines outlined in this article, you can significantly enhance the protection of your RPi3 VNC server.
We encourage you to apply these practices and share your experiences in the comments below. For further reading, explore our other articles on Raspberry Pi security and remote access solutions. Together, let's build a safer digital environment.
Table of Contents
- Understanding the Importance of Security for RPi3 VNC Server
- Basic Security Measures for RPi3 VNC Server
- Advanced Security Configurations for RPi3 VNC Server
- Firewall Configuration for Enhanced Security
- User Access Management for RPi3 VNC Server
- Regular Updates and Patch Management
- Monitoring and Logging for RPi3 VNC Server
- Backup Strategies for RPi3 VNC Server
- Testing Security Configurations
- Best Practices for Long-Term Security
References:
- Official Raspberry Pi Documentation
- VNC Server Security Best Practices
- National Institute of Standards and Technology (NIST) Guidelines